How to Evaluate Products for Secure IoT Remote Access?
Save valuable time and resources. Learn how to evaluate products for secure IoT remote access!
Read our 4-step guide for the successful selection of a remote access solution for IoT devices:
STEP 1: Internal Company Analysis
Why it is important to strategically set a technology pathway?
Before choosing or implementing a remote access solution, you should have a clear idea of why you need a remote access solution, and what you want to achieve. You need to define your goals, needs, options and steps for choosing a remote access solution to ensure that you end up with a solution that fits your requirements perfectly and stays within your budget.
Critical Questions
By answering following questions, you will be able to clarify your business goal with remote access and choose the best solution for your situation:
What do you want to access remotely?
- Access the to the device’s web user interface or REST APIs
- Access to the devices screen and graphical user interface via screen-sharing (VNC or RDP)
- Access to the device’s command-line shell via SSH for troubleshooting
- Access to the device via industrial protocols (e.g., Modbus TCP, OPC UA) or custom protocols (e.g., engineering tool to PLC)
How many devices will have to be connected?
- 10s to 100s
- A few 1000s
- 100.000s or millions
Who should be able to remotely access devices?
- End users of the device
- Sales and service partners supporting customers in setting up and maintaining devices
- Internal staff
Is fine-grained access control required?
- Should every user be able to access all devices?
- Does access to devices need to be controlled in detail (e.g., specifically for each user which devices or ports can be accessed)?
Explore our complimentary eBook to uncover other key questions that will help you define your business goals with remote access.
STEP 2: Remote Access Technologies
Your internal company analysis, carried out in step one, will guide you to the technology that best meets your requirements. There are several types of used remote access technologies available to companies, each with its own advantages and disadvantages.
Understanding the strategic use of widely used remote access technologies such as Secure Tunneling (macchina.io REMOTE), Port Forwarding and VPN (Virtual Private Network) is crucial for selecting optimal IOT remote access solution.
Secure Tunneling (macchina.io REMOTE)
When to use?
- Access to specific remote devices and ports (services) is required. No changes to existing network configuration at remote site are possible.
- Fine-grained access control for different user groups is needed.
- Must scale to 100.000s or millions of devices.
Port Forwarding
When to use? Access to a single device (or a very small number of devices) behind a router when security does not matter.
VPN (Virtual Private Network)
When to use? Access to an entire remote network is required.
STEP 3: Available Solutions
How do you choose the best solution for your needs and preferences?
To help you with this decision, we have prepared, in our complementary eBook as well in our free Worksheet for Comparing Remote Access Solutions (Excel), a table that gives you a list of criteria to compare and evaluate products for secure IoT remote access against each other.
The table covers various aspects of remote access, such as licensing and delivery, technology, features, security, infrastructure, documentation, branding, integration and many more.
Here’s an insight into some of the comparison criteria:
| COMPARE AVAILABLE REMOTE ACCESS SOLUTIONS | |||
| CRITERIA | SOLUTION A | SOLUTION B | SOLUTION C |
| Solution | macchina.io REMOTE | ||
| Licensing and Delivery | Combined proprietary (server) and open source (device agent, SDK) | ||
| Technology | WebTunnel (secure tunnel over WebSocket/HTTPS/TLS) | ||
| Self-hosted/on-prem | YES | ||
| Software-only Solution | Independent from hardware providers | ||
| Free plan | ✓up to 10 connections are free of charge | ||
| Scalability | 10s to millions of devices (load-balancing and server clustering) | ||
| Security | Encrypted connections (TLS), device authentication via secrets or certificates | ||
| Role-Based Access Control | YES | ||
| Find-Grained Access Control to Devices | ✓ (single device and port/service level per user) | ||
| Time for integration | 2 – 4 hours | ||
You can find many more in our free Worksheet for Comparing Remote Access Solutions (Excel), which includes macchina.io REMOTE as an illustration.
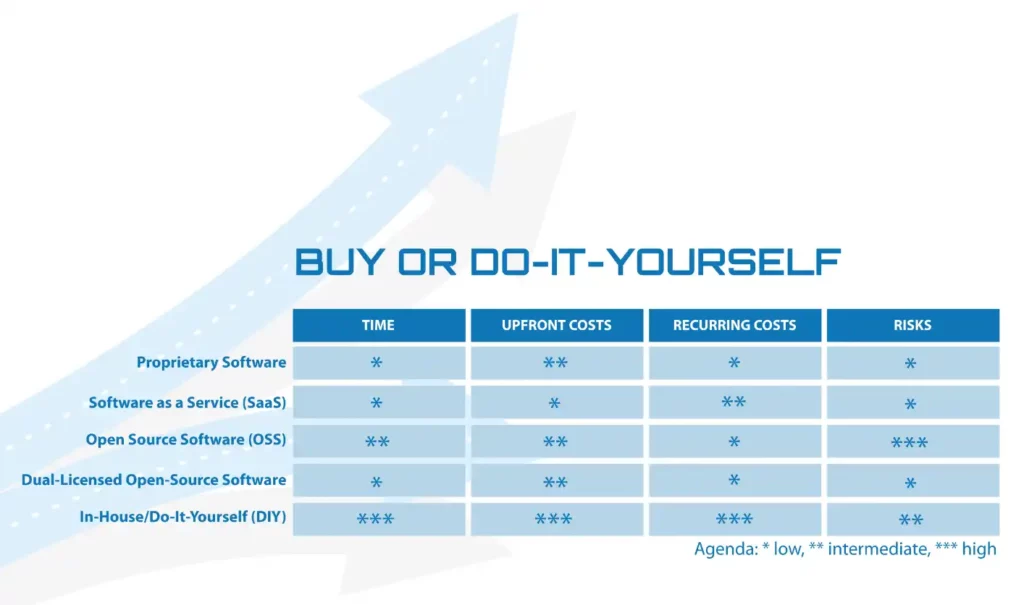
STEP 4: Buy or Do-it-Yourself
After completing the previous steps, you should have a clear idea of
• your internal requirements and capabilities
• the appropriate remote access technology and
• the available solutions on the market.
Before you decide, whether to
• use an off-the-shelf one or
• build your own solution
let us discuss the following forms for licensing and delivery:
• Proprietary Software
• Software as a Service (SaaS)
• Open Source Software (OSS)
• Dual-licensed Open Source Software
• In-House / Do-It-Yourself
We have compared all forms of licensing and delivery based on the most important factors that affect your project budget, implementation time and risks.
LOOKING FOR SECURE ACCESS AND CONTROL TO YOUR IOT DEVICES?
Remote access to IoT devices behind a firewall is now easier than ever!
- Made in EU
- Open source SDK and device agent
- Self-hosted (on-prem or any cloud provider)
- Customize and integrate into your environment
- Pay only for what you use
- Powerful and resource efficient
- Access and control more than 100,000 devices
- Zero direct attack possibility
