Remote Access to IoT: A Case Study for Telephony Systems
REMOTE ACCESS FOR SERVICE PARTNERS
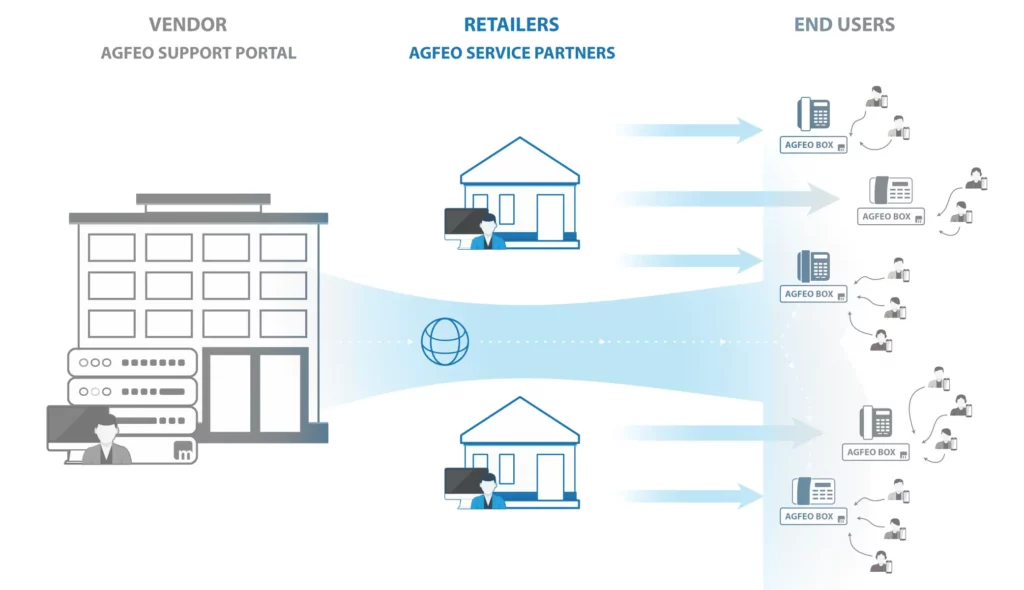
GOAL: Help service partners avoid the hassle of setting up complex remote access solutions and give them always accessible way to connect to their customer’s phone systems remotely.
What did we do?
- Enabled remote access for service partners.
- Enabled remote maintenance of their customer’s PBX systems
- Allow to grant (temporary) access to additional users (vacation mode*)
- Enabled remote user access management
*vacation mode
Don’t you hate it when your service partner is on vacation and you need them urgently?
With macchina.io REMOTE you don’t have to worry about that anymore!
macchina.io REMOTE allows service partners to delegate access to trusted external partners (vacation mode), ensuring no downtime and timely service to end users.
By integrating our versatile and easy to use remote access solution, macchina.io REMOTE has enabled service partners to access their customers’ telephony systems securely and effortlessly.
Service partners can now enjoy the convenience of secure remote access to PBX systems. This means they can configure and troubleshoot PBX systems remotely, without having to visit the site physically. How cool is that?
This results in cost savings for end users and significantly improved quality of service and support.
They can also monitor and manage multiple PBX systems from one dashboard, making life easier and more efficient.
No need to set up complex customized remote access software. No need to worry about data breaches or unauthorized access.
Just plug and play with macchina.io REMOTE.
AGFEO saved money and resources, and service partners saved time and energy.
Check out our other Case Study posts on Agfeo Telephony Systems and get information:
FULL CONTROL OVER PBX SYSTEMS AND IOT DEVICES FROM ANYWHERE IN THE WORLD!
Remote IoT device access behind a firewall is now easier than ever!
- Made in EU
- Open source SDK and device agent
- Self-hosted (on-prem or any cloud provider)
- Customize and integrate into your environment
- Pay only for what you use
- Powerful and resource efficient
- Access and control more than 100,000 devices
- Zero direct attack possibility
- Fine grained access control
- Multi factor authentication
