For running the macchina.io REMOTE server (also known as reflector server), a wildcard certificate is required. Wildcard certificates have become quite expensive recently. While it was possible to buy one for about 250 $, minimum prices seem to have doubled in recent months. However, it’s not necessary to buy a wildcard certificate. A free wildcard […]
None of our products are implemented with Java and do not use log4j. Therefore, none of our products are affected by the recently discovered Remote Code Execution vulnerability (CVE-2021-44228) in the Apache Log4j logging utility. Furthermore, we have also checked our software supply chain, and none of the tools we use are affected by this […]
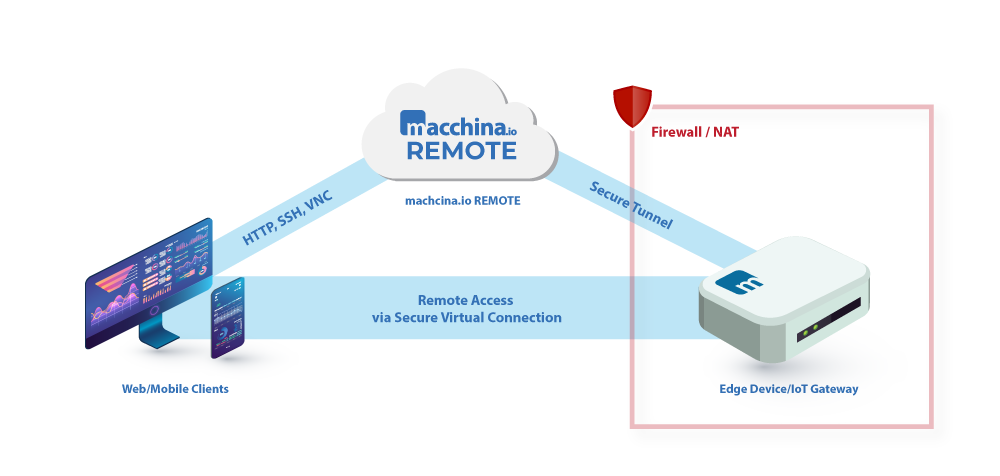
Secure remote access to IoT edge devices is one of the fundamental building blocks of the Internet of Things. End users want to access and manage their devices via web or mobile app, service partners need access to devices installed at remote locations, and product sup-port teams need to be able to log-in to devices installed at customer sites.
Today we’re releasing version 2.4.0 of macchina.io Remote Manager. The most important feature in this release is support for two-factor authentication using time-based one-time passwords (TOTPs), such as supported by apps like Google Authenticator or Authy. If enabled in the global application configuration, a user can set up two-factor authentication in their account page in […]
macchina.io Remote Manager provides secure remote access to connected devices – for end users, service providers and support teams. Setting up your own macchina.io Remote Manager server on Amazon AWS is now easier than ever. We now provide a pre-configured AMI (Amazon Machine Image) which has everything required to run the Remote Manager server preinstalled and […]
Secure remote access to IoT edge devices is one of the fundamental requirements of the Internet of Things. IoT devices are often located in places that cannot be reached easily by support technicians, such as remote locations or factory floors with access restrictions. Nevertheless, it must be possible for support staff and other authorized staff […]
Linux-based single-board computers like the Raspberry Pi, BeagleBone, RED Brick, UDOO, Galileo or Cubieboard are very popular choices in the Maker scene for building all kinds of devices needing plenty of computing power and internet connectivity – the Things in the so-called Internet of Things. And not just in the Maker scene – these low-cost, […]
On April 7, a team of security researchers found a critical bug in some versions of OpenSSL that allow an attacker to read random memory regions of affected server processes. This issue is widely known as Heartbleed, and more formally as CVE-2014-0160. Immediately after becoming aware of the issue, we have checked the server hosting […]
Various vendors of network-connected devices, specifically in home automation, use port forwarding and Dynamic DNS as a means to provide remote access to their devices, both for end users and for remote service purposes. However, as a recent case in Germany showed, this is a very bad idea as it opens the door for various […]